Ben Reich, proprietor of Monarch Utilities & Resources, Inc. is shopping for an earworm. A common commercial hook won’t do. Mr. Reich needs an industrial-strength jingle, Top 40 vintage. His earworm isn’t meant to climb charts or sell mobile phones; it is part of the businessman’s latest venture, a project no one has engaged in for more than seventy years: plotting a murder. In Reich’s century, the twenty-fourth, telepathy has somehow become commonplace, and murders are impossible. Policemen, marketing gurus, personal assistants, rival businessmen, a whole class of humanity, is an “Esper,” reading conscious and unconscious thoughts alike. An earworm, then, runs perfect cognitive interference for a corner-office sociopath. With a looping melody firmly embedded in Reich’s wetware, the businessman is free to plot an assassination, all the while exuding pop song mania to anyone who cares to eavesdrop.
This is the set-up for Alfred Bester’s 1953 novel, The Demolished Man, an early literary rehearsal of decades of cyberpunk to come. Even on the edge of Eisenhower’s America, former PR-man Bester was captivated by the parasitic intensities of popular music. The word “earworm” appeared later – in 1991, according to the Oxford English Dictionary. Earworm: from the German, Ohrwurm, meaning the same as it would come to mean in English, an infectious, viral bit of music holding short-term memory and attention hostage. An effective earworm, like any meme, must also move quickly through populations, transmissible by humming only a few notes. If the virus is the social metaphor for cultural transmission, then the worm is its more complex multicellular adjunct. An earworm proliferates, but it also must burrow, dig in, becoming an unwelcome neurological lodger. Its life is doubled, pleasurable and uninvited.
This double life has echoes elsewhere, namely in the history of distributed computing. It is said that science fiction does not always attempt to predict the future; it amplifies qualities of the present. Bester did not predict the colonizing of mental space by popular culture – it already existed, though with less intensity than it does today. He also did not give his earworms algorithmic form. Instead, Reich relies on the brilliance of a songwriter. It would take the 1975 novel, The Shockwave Rider, by British author John Brunner to imagine a digital worm, not as a marketing ploy or a cover for murder, but as a means of escape. Brunner, transfixed by Alvin Toffler’s futurism, devised perhaps the first hacker anti-hero, Nick Haflinger, who would use a digital “tapeworm” to evade technocratic surveillance. In this case, contrary to the earworm, the tapeworm was used as a vehicle for dissociation and guile, followed by periods of “digging in” under assumed identities:
What I turned loose in the net yesterday was the father and mother of all tapeworms… My newest – my masterpiece – breeds by itself… By now I don’t know exactly what there is in the worm. More bits are being added automatically as it works its way to places I never dared guess existed… And –no, it can’t be killed. It’s indefinitely self-perpetuating so long as the net exists. Even if one segment of it is inactivated, a counterpart of the missing portion will remain in store at some other station and the worm will automatically subdivide and send a duplicate head to collect the spare groups and restore them to their proper place.
Brunner’s psychedelic sci-fi found a computational embodiment in a likely place: Cambridge Massachusetts’s BBN Technologies. Begun as an acoustics consulting firm after the Second World War, Bolt, Beranek, and Newman (later BBN, and now Raytheon BBN) quickly expanded into computing and artificial intelligence research. Over the following decades, the company, sometimes called Cambridge’s “third university,” invented such crucial Internet technologies as packet switching, Transmission Control Protocol (TCP), and telnet, as well as an early implementation of secure packet transmission.
One other invention is left off most compilations, official and otherwise: BBN produced the first Internet “worm,” Creeper. In 1971, programmer Robert H. (Bob) Thomas, while developing the operating system TENEX, wrote a small program to demonstrate “mobile code.” The program announced itself on the display to a user, began printing a file, then stopped and copied itself to another machine. The ability of the software to replicate and become mobile was limited by the fact that the algorithm deleted the previous version when finished, therefore guaranteeing only one Creeper existed on a given network. According to Thomas’s colleague, Ray Tomlinson, inventor of email, this duplicate-delete-repeat algorithm was meant to investigate how applications might intelligently move across a network in order to best exploit computational resources. He explains: “For example, it might be preferable to move the application to the machine having the data (as opposed to bringing the data to the applications).”
The unintended consequence of this research was an “arms race” between Creeper and a second program, “Reaper,” a worm created at BBN in order to remove Creeper from the system. Software like Reaper is sometimes referred to as a “nematode” – in agriculture, a round or un-segmented worm sometimes used to kill pests. Unlike typical anti-virus software, a nematode is not welcomed into a system. It uses the same manner of exploitation, entry, and proliferation as a worm, with one difference: it exists to eradicate other worms. To date, the practice of releasing nematodes into the wild is considered unethical, and, more importantly, much contemporary malware does this service anyway – sophisticated malware will often clear systems of competitors in order to increase the probability of smooth survival.
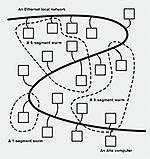
The 1971 Creeper was endemic to ARPANET, the Advanced Research Projects Agency Network. This was a Defense Department-funded proto-Internet linking together computers at universities, government agencies, and private companies across the United States. Each organization on the network contained a number of ‘nodes’ – endpoints on the network – and each of these nodes was linked by leased telecommunication lines, or “leased lines.” A twenty-first-century Creeper could burrow worldwide in hours, but because ARPANET was used only among a relatively small number of institutions, Creeper’s existence was slightly more than hearsay. It was only in 1982 that Creeper was pinned with the taxonomic label “worm,” thus becoming known to a slightly wider audience. The taxonomists were John F. Shoch and Jon A. Hupp, computer scientists and admirers of Brunner’s hacker. As they describe in their paper “The ‘Worm’ Programs – Early Experience with a Distributed Computation,” Shoch and Hupp’s worms flourished in the research offices of Xerox’s Palo Alto Research Center (PARC). Like BBN, Xerox PARC is a pageant of firsts: the first graphical user interface, the first WYSIWYG (What You See Is What You Get) application, the first laser printer. Another two ‘firsts’ – the Alto, the first individual-scale computer, and the first Ethernet network – provided their worm’s soil. Unlike Creeper, existing on one machine at a time, the Alto worm proliferated across machines, each copy called a “segment.” A segment began on one Alto and then inspected the network for an Alto with free memory. If a machine responded positively, the segment copied a new segment to the second Alto. When complete, the new segment maintained communication with the previous segment, and, by implication, all other segments. The process was then repeated, repeated, repeated again….
These first primitive segments were “null programs” – they did nothing but inspect and machine hop without announcing their arrival on a new host. Silent and epidemic, one early test run at PARC crashed the in-house network overnight, taking down more than a hundred machines. The authors wrote, perhaps delighted: “At this point, one begins to imagine a scene straight out of Brunner’s novel – workers running around the building, fruitlessly trying to chase the worm and stop it before it moves somewhere else.”
Somehow, the press noticed, notably The Christian Science Monitor, all alarms sounding: “If one of these machines were restarted, it would soon be invaded by WORM [sic] again. Every invaded computer on a network must be cleared and reprogrammed to get rid of the menace.” The network needed clearing, yes, but Shoch and Hupp did not mention any “reprogramming” in their paper. More importantly, did Shoch and Hupp intend to create a menace? Probably not. Like Creeper, the PARC worms were not anarchic software. They were the crude first maps of a new territory: distributed computing. The problem for Shoch and Hupp was not how to destroy more machines, but how to keep their worms’ migrations under control. More sophisticated later worms kept infected Altos running, with segments maintaining an updated log of all colonized Altos, in a manner similar to how routing tables are kept in packet switching networks. (ARPANET, for example, used a number of proto-routers, Interface Message Processors, built on similar algorithms.) Tamed, the PARC worm segments expanded their population at night when programmers went home, thus freeing computational resources, and would then reduce their segments in the morning when programmers were back at their desks. Depending on which experiment Shoch and Hupp conducted, resources were farmed out to computers in parallel, thus harnessing the computation power of an entire network at one time. In one experiment, Shoch and Hupp used parallel processing to render graphics across the network, turning each computer into a “worker” processor. (A technique similar to the later SETI@home software that harnesses millions of PCs to search for extraterrestrial radio signals.) Another experiment created a worm-driven alarm clock to wake employees with a telephone courtesy call – a good test of how many machines could keep the state of the whole system in sync at one time. (Has this user been called? At what time? By which machine?) Software would no longer be constrained by one machine, one hardware configuration. It would become a ubiquitous computation.
“Worm” tunneled into history, the invertebrate metaphor of choice. But then there are the metaphors not used, never developed. A PARC colleague of Shoch and Hupp suggested “vampire programs,” Bela Lugosis of the computer lab. Shoch and Hupp, their love for science fiction already proven, instead suggested their creations were like the gelatinous creature from The Blob (1958) – expanding and contracting when needed, filling free space with an electronic plasma. One might hear a murmur from a different source, too: Georges Bataille, who probably never saw a computer; whose preoccupations were more for the occult, who wrote of l’informe, or the “formless,” a countermovement to modernism’s order and proportion. “What it designates has no rights in any sense and gets itself squashed everywhere, like a spider or an earthworm. In fact, for academic men to be happy, the universe would have to take shape […] It is a matter of giving a frock coat to what is, a mathematical frock coat.”
Frock coats or not, Shoch and Hupp had not read of Bataille’s informe. They did better; they created it themselves. Shoch and Hupp showed that computer science is as capable of producing uncanny organisms as those of Surrealism and Hollywood B-movies. Science has always, and perhaps will always, lead this double life. A life in search of the real that often finds a necessary surrogate instead – the horrifying. The worm research of Shoch and Hupp went on to live exactly this double life over the next decades. Distributed computation came to rule Silicon Valley engineering, powering most major corporate and government projects, being sold as a service through Amazon Web Services, Google App Engine, and others. Then it also gave life to criminal botnets and Internet-crippling worms like Conficker, which infected millions of computers in hundreds of countries starting in 2008. Sharing ancestors under PARC’s drop ceilings and dustless computer rooms, worms bifurcated, becoming a rational administrator for capital and a frenzied insurgent for its destruction.